Is it really useful to have multiple variants of the ransomware network cable?
2023-12-24 06:07:37
On May 15, the head of the Network Security Coordination Bureau of the Central Network Office responded to the "worm" ransomware attack, saying that the ransomware is still spreading, but the speed of transmission has slowed down noticeably. At the same time, the National Network and Information Security Information Center found that there were several variants of the WannaCry ransomware, such as changes in the switch domain name and changes in the money collection address, but the main communication mechanisms and methods of destruction did not change, and the threat still existed.
After the virus intrusion incident, the multi-network security device released a plan to deal with the virus "attack": first unplug the network cable, install the patch, and then back up the file after networking, and then get widely forwarded by netizens. Network security expert Zheng Wenbin told the squad on the 37th. The key to this approach is to fix the system vulnerabilities by installing patches and other patches in time.

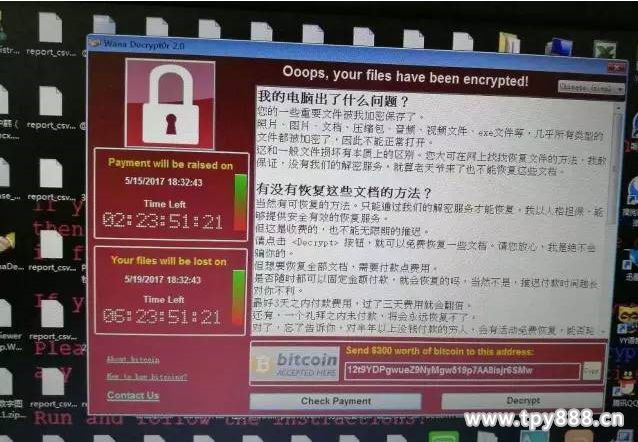
A computer that has been "infected" by a ransomware receives a "blackmail" that requires $300 worth of bitcoin to unlock the document.
A computer that is "infected" by a ransomware receives a "blackmail letter" with a bitcoin equivalent to $300 equivalent to unlock the document.
Multi-site gas station network recovery bank reinforcement firewall
The squadron reported on the 37th that netizens said that on the 12th, the CNPC gas station in many parts of the country could not make online payment when refueling, and only used cash. According to the report of Chinanews.com, the relevant person in charge of PetroChina said that the refueling business and cash payment business of the company's gas station are operating normally, but the third-party payment cannot be used, and it is suspected of being attacked by the virus. The specific situation is still being verified.
On the afternoon of May 15, the squadron of the squadron No. 37 was informed by a staff member at the gas station of Huawei South Road, PetroChina, that the gas station had returned to normal on the 13th, and it could be swiped by bank card. The function of the fuel card was also It has returned to normal.
According to the squadron No. 37, the staff of several gas stations in Beijing, Tianjin and Hebei confirmed that the network of gas stations will resume normal after 13-15 days, and they can be consumed by credit card. "Most of China's PetroChina gas stations have resumed network connections, and fuel card, bank card, and third-party payment functions have been restored." A gas station staff said.
At the same time, the squadron No. 37 agents learned from many banks in Beijing, Nanjing, Hangzhou and other places that some banks installed firewalls and patches in time to fix the system's loopholes in order to prevent them from happening. A staff member of Beijing Huaxia Bank said that after the virus intrusion incident, in addition to not being able to download files on the intranet, the background system runs as usual, but it has now been restored. Nanjing CITIC, Hangzhou Zheshang and an agricultural bank in Foshan, Guangdong, said that the bank did not have a virus intrusion and took measures to protect it. At present, the back-end system repair is completed and will not affect the daily business.
Preventive measures for statistical virus intrusion data release in colleges and universities
On May 15th, for the spread of Bitcoin ransom virus in colleges and universities, Shandong University and Nanchang University Undergraduate School published information on computer poisoning of students. Zhejiang Information Office helped students reinstall the system and eliminate hidden dangers for students.
Zhao, a journalism major at Nanchang University, said that when the campus network was connected at 8:00 on the morning of the 12th, the computer was suddenly attacked. His English courseware could not be opened. After that, the school issued a notice about the intrusion of ransomware. He said that there was no important document. Encrypted, all files have been backed up, and the system is currently being reinstalled. The Management Department of Nanchang University also said that the college is also inquiring about the specific circumstances of the student computer being attacked, and the follow-up arrangements have to wait for the statistics to be completed.
On the morning of the 15th, the head of the Propaganda Department of Shandong University said that at around 20 o'clock on May 12, a large-scale ransomware infection incident based on the Windows platform broke out in the world. Some of the students' computers in our school were also attacked by ransomware and the data was damaged. In order to further guide students to take precautions against viruses, the colleges are required to promptly inform students to update the operating system patches as soon as possible according to the official notice. At the same time, please do a thorough investigation of the damage caused by the ransomware virus caused by the student's computer data, especially the statistics on the damage of the graduation thesis of the graduating students, and strengthen the attention and appeasement of the relevant students.
Zhou Haifeng, director of the Information Office of Zhejiang Media College, told the Crime Squad, No. 37. Some students were infected with ransomware on their computers. They went to the information office to find a teacher. The teacher would help the students to re-do the system. For computers that are not infected with the virus, the school is also helping students to do some protective measures for the computer, such as installing patches.
Detective questioning
  "Stop the network and then boot" to stop the virus?
On May 15, Hainan Province Net Security issued a security notice saying that the ransomware virus broke out. All units first pulled the network cable on Monday, installed the Windows patch, and then backed up the file before opening the computer. Later, Shenzhen, Chongqing Netan, Chengdu City Committee Network Office, etc. also issued similar notices to answer specific measures to prevent ransomware. In Weibo and friends circle, the information of “disconnecting the network first and then turning it on†was widely forwarded by netizens.
Network security expert Zheng Wenbin explained to the Serious Crimes Committee No. 37 that this program is indeed feasible. Because non-professionals, individuals can not determine whether the computer is open 445 and other ports, you can first unplug the network cable, block the virus intrusion, then install the patch, then back up the file, and finally re-network. But the most important thing is to upgrade the computer system or install patches using the CD as soon as possible to fix system vulnerabilities.
How to prevent ransomware after a variant?
Xie Xin, a network security expert, explained that as long as the following win10 systems (xp, win7, win8, win2003, win2008) are not updated, the dangers of being attacked will definitely continue to spread, and as other hackers understand the principle, new Variants or new ransom family will become more diverse. The most secure way to prevent it is to close port 445, which is to set the firewall policy mode by shutting down the service, but it will also cause some software or computer functions that rely on port 445 to fail.
Wang Lingling, a network security expert, believes that from the past attacks, there is a high possibility of variants, but as long as the system patch is properly installed and the high-risk port is closed according to the security agency's reminder, the virus's transmission can be controlled.
    Why did the attack expand from universities to banks and other systems?
Wang Ziling explained that this virus intrusion first targeted computers such as colleges and universities that exposed 445 high-risk ports, and then further entered the intranets of certain institutions, causing great damage to the internal network. These attacked internal network computers must be unpatched or not closed 445 ports, and the internal network computers have no security protection between each other, so the fall is particularly fast.
Xie Xin added that the virus started to spread on Friday afternoon. The time period was basically in the off-duty state. On Saturday, it began to spread widely. The universities and institutions that were attacked were mostly connected on the weekend.
  What are the hidden risks of paying Bitcoin “ransom�
Wang Ziling explained that most security agencies do not recommend paying ransoms, because this virus intrusion is not a peer-to-peer attack. Some computers connected to the intranet are vulnerable to infection, but not every computer has a decrypted password. Hackers can't fully grasp the situation of infected computers, and individuals who pay ransoms may not get the decryption key.
Toilet with Sink On Top,Hand Held Shower 3 Function,Mixer Tap with Hand Shower,Hand Shower Set,Hand Shower Batroom,ABS Hand Showers,Hand Shower Ion
Yuyao Gaobao Sanitary Ware Factory , https://www.gurberry.com